RescueRanger
PDF THINK TANK: CONSULTANT

- Joined
- Sep 20, 2008
- Messages
- 16,370
- Reaction score
- 244
- Country
- Location
Earlier this year in April, Pakistani hacker group Transparent Tribe used a 2FA (Two factor authentication tool) used by the Indian Government to install a Linux backdoor Poseidon.
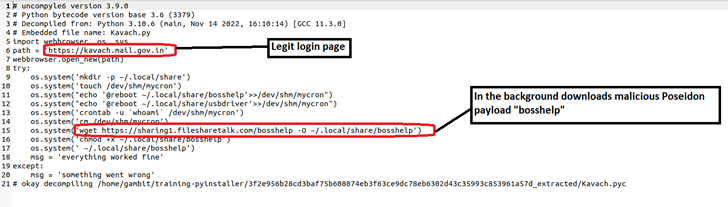
Poseidon is a general-purpose backdoor that provides attackers with a wide range of capabilities to hijack an infected host. Its functionalities include logging keystrokes, taking screen captures, uploading and downloading files, and remotely administering the system in various ways.
The Pakistan hacker group known as SideCopy has been observed leveraging the recent WinRAR security vulnerability in its attacks targeting Indian government entities to deliver various remote access trojans such as AllaKore RAT, Ares RAT, and DRat.
Earlier this May, the group was linked to a phishing campaign that took advantage of lures related to India's Defence Research and Development Organization (DRDO) to deliver information-stealing malware.
Since then, SideCopy has also been implicated in a set of phishing attacks targeting the Indian defense sector with ZIP archive attachments to propagate Action RAT and a new .NET-based trojan that supports 18 different commands.
The new phishing campaigns detected by SEQRITE entail two different attack chains, each targeting Linux and Windows operating systems.

The former revolves around a Golang-based ELF binary that paves the way for a Linux version of Ares RAT that's capable of enumerating files, taking screenshots, and file downloading and uploading, among others.
The second campaign, on the other hand, entails the exploitation of CVE-2023-38831, a security flaw in the WinRAR archiving tool, to trigger the execution of malicious code, leading to the deployment of AllaKore RAT, Ares RAT, and two new trojans called DRat and Key RAT.
"[AllaKore RAT] has the functionality to steal system information, keylogging, take screenshots, upload & download files, and take the remote access of the victim machine to send commands and upload stolen data to the C2,"
According to TalosCISCO security research: Analysis of the log files generated by the PHP pages was able to identify around 400 unique IPs, most of which were concentrated in India. Some of these IPs were attributed to Indian governmental and civil organisations by analysing the information contained in the Whois registry databases. For example:
– M.P. Power Management Company Limited
– Power System Operation Corporation Limited
– Inspector General of Police
– Chief of Naval Staff
– National Remote Sensing Agency.
Transparent Tribe has been using a fake Facebook and Youtube App to spread CapaRAT malware among targets in India:

By using malicious Android apps mimicking YouTube to distribute the CapraRAT mobile remote access trojan (RAT), demonstrating the continued evolution of the activity. "CapraRAT is a highly invasive tool that gives the attacker control over much of the data on the Android devices that it infects," SentinelOne security researcher Alex Delamotte said in a Monday analysis.
Transparent Tribe, also known as APT36, is known to target Indian entities for intelligence-gathering purposes, relying on an arsenal of tools capable of infiltrating Windows, Linux, and Android systems.
Poseidon is a general-purpose backdoor that provides attackers with a wide range of capabilities to hijack an infected host. Its functionalities include logging keystrokes, taking screen captures, uploading and downloading files, and remotely administering the system in various ways.
The Pakistan hacker group known as SideCopy has been observed leveraging the recent WinRAR security vulnerability in its attacks targeting Indian government entities to deliver various remote access trojans such as AllaKore RAT, Ares RAT, and DRat.
Earlier this May, the group was linked to a phishing campaign that took advantage of lures related to India's Defence Research and Development Organization (DRDO) to deliver information-stealing malware.
Since then, SideCopy has also been implicated in a set of phishing attacks targeting the Indian defense sector with ZIP archive attachments to propagate Action RAT and a new .NET-based trojan that supports 18 different commands.
The new phishing campaigns detected by SEQRITE entail two different attack chains, each targeting Linux and Windows operating systems.
The former revolves around a Golang-based ELF binary that paves the way for a Linux version of Ares RAT that's capable of enumerating files, taking screenshots, and file downloading and uploading, among others.
The second campaign, on the other hand, entails the exploitation of CVE-2023-38831, a security flaw in the WinRAR archiving tool, to trigger the execution of malicious code, leading to the deployment of AllaKore RAT, Ares RAT, and two new trojans called DRat and Key RAT.
"[AllaKore RAT] has the functionality to steal system information, keylogging, take screenshots, upload & download files, and take the remote access of the victim machine to send commands and upload stolen data to the C2,"
According to TalosCISCO security research: Analysis of the log files generated by the PHP pages was able to identify around 400 unique IPs, most of which were concentrated in India. Some of these IPs were attributed to Indian governmental and civil organisations by analysing the information contained in the Whois registry databases. For example:
– M.P. Power Management Company Limited
– Power System Operation Corporation Limited
– Inspector General of Police
– Chief of Naval Staff
– National Remote Sensing Agency.
Transparent Tribe has been using a fake Facebook and Youtube App to spread CapaRAT malware among targets in India:
By using malicious Android apps mimicking YouTube to distribute the CapraRAT mobile remote access trojan (RAT), demonstrating the continued evolution of the activity. "CapraRAT is a highly invasive tool that gives the attacker control over much of the data on the Android devices that it infects," SentinelOne security researcher Alex Delamotte said in a Monday analysis.
Transparent Tribe, also known as APT36, is known to target Indian entities for intelligence-gathering purposes, relying on an arsenal of tools capable of infiltrating Windows, Linux, and Android systems.
